As the holiday season has ramped up, so has the online hacking/phishing of accounts that are connected to your bank accounts, credit cards and debit cards. Reports of the latest phishing for Amazon and Paypal are just two of the ongoing attempts that are used to steal money from your account. Here are a few […]
The basic premise of search engine reputation management is to use the following three strategies to accomplish the goal of creating a completely positive first page of search engine results for a specific term…
As a technology firm, Phoenix Consultants Group looks deeply at any releases that could compromise computer systems or personal electronics. The recent technical information provided by Wikileaks is astounding, to say the least, as to the unknown infiltration into technology that has been developed through many of these programs. It is safe to say that […]
I recently was reminded through the movie Snowden of the critical need to cover your webcams. Most people leave their cameras open and running on their computers, laptops and phones. In today’s world, this gives the perfect opening for a hacker or person who does not have your best interests at heart to see and […]
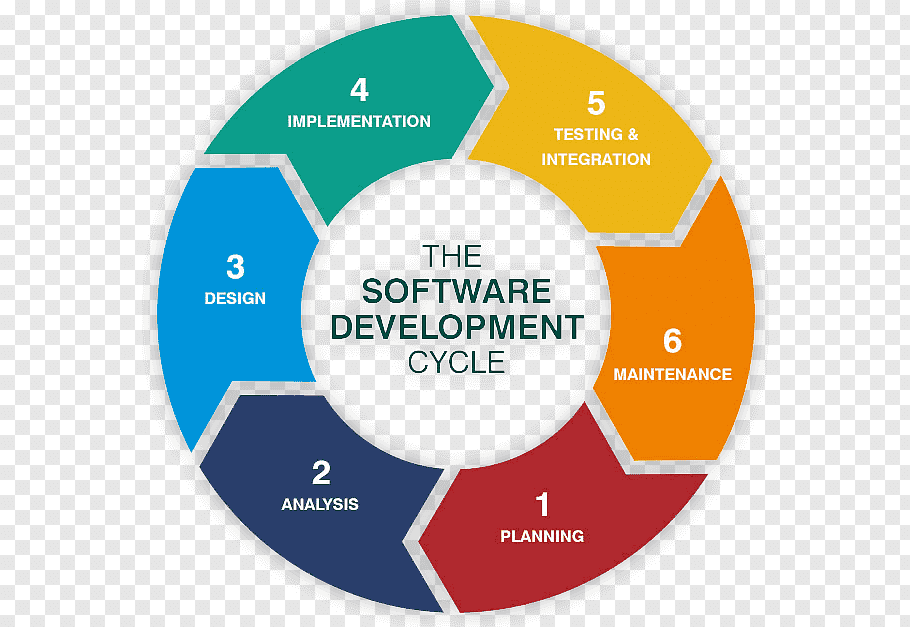
The complete software development process, or Software Development Life Cycle, is the process of creating or changing software systems and the methodologies that are used to achieve the changes. In the world of software engineering, SDLC underlines various types of development methodologies. These methodologies combine together to form a skeleton of planning, control and execution, which is globally known […]
- 1
- 2